Understanding Auto-Upgrade Options in Azure AD Connect
For hybrid customers, Azure Active Directory Connect is one of the most important tools you need to...

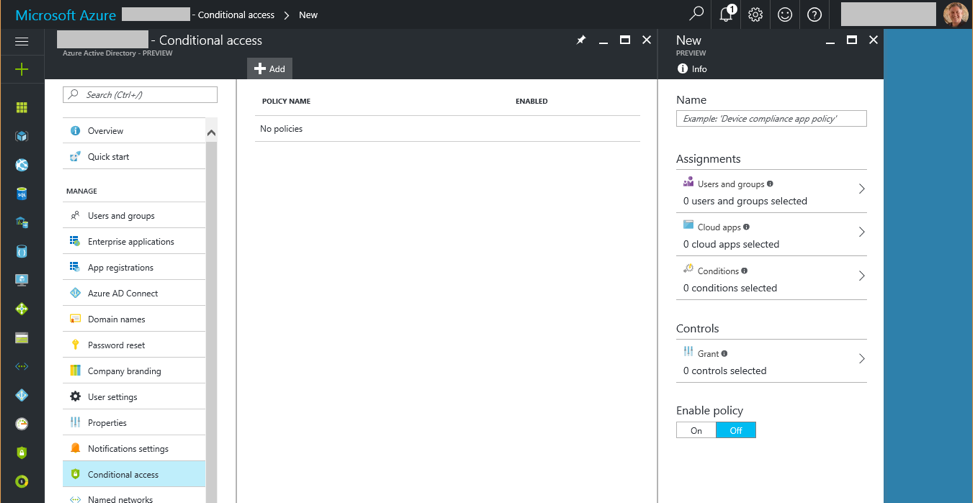
There have been some questions on the Office 365 and Microsoft Azure LinkedIn forum regarding conditional access and pass-through authentication. Will it work? What are the requirements? Some confusion comes from this article, that implies pass-through authentication by itself allows for conditional access. Conditional access will work with pass-through authentication if your client applications support modern authentication and you have Azure AD Premium. Let’s break it down further.
Conditional access controls how and when clients can access Office 365 resources, including email or SharePoint Online. Allowing employees to access their email only within the corporate network is one example of conditional access.
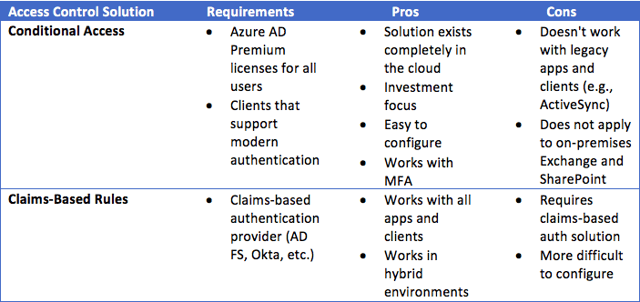
There are two types of conditional access. The first (and older) way is to use claims rules — it requires a claims-based authentication solution, such as AD FS on-premises, Azure AD Premium or a third-party claims-based solution like Okta or Ping Identity. For example, using AD FS, the administrator can create a claims rule generating a valid SAML token only when the client is accessing the resource from the internal corporate network. The type of client application, such as Outlook, OWA or ActiveSync device, can be specified in the rule. Claims rules are used to develop complex requirements for access control. See an AD FS Claims Rules Adventure on the Ask Directory Services Team blog for real-world examples.
The second option is to use Azure AD Conditional Access. Conditional access policies for Exchange Online and SharePoint Online allow you to easily configure things like multi-factor authentication (MFA) or allowing access based on network location. These policies are much easier to configure than claims rules since you can use a simple GUI in the Azure management portal that doesn’t require scripting. Microsoft will be making the most investments in conditional access, but you should know the requirements, prerequisites and capabilities.
Azure AD Conditional Access requires that organizations have an Azure AD Premium license for each user who has a conditional access policy applied to them. As of November 2016, there are two types of Azure AD Premium licenses – P1 and P2. Both work for conditional access. If your users are licensed for Enterprise Mobility + Security (EM+S) E3 or E5, they already have licenses for Azure AD Premium.
With Office 365, conditional access only works for clients that support modern authentication (ADAL). This includes Office 2016 (Outlook, Word, Excel, PowerPoint and OneNote), Office 2013 (with modern authentication enabled), the OneDrive sync client (with modern authentication) and most modern mobile apps such as Outlook, Word, Excel, PowerPoint and Skype for Business for iOS and Android.
There are no plans for Office 2010, Office 2007 or other legacy applications to support modern authentication. ActiveSync also does not support modern authentication. These limitations mean that unless you block these applications, or configure your tenant to only use modern authentication, legacy applications will be able to connect and bypass conditional access rules. If you block legacy applications, ActiveSync devices will no longer connect and your users will need to use Outlook Mobile (iOS or Android) instead.
You should also understand that conditional access only works when accessing Office 365 resources. For hybrid customers, conditional access rules will not apply to on-premises users accessing on-premises applications like Exchange or SharePoint.
You configure modern authentication and conditional access in your tenant using a combination of the Azure management portal and PowerShell.
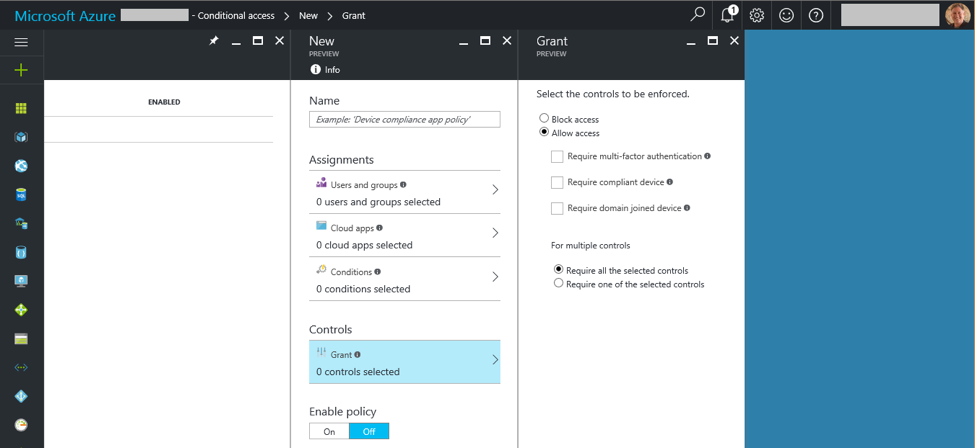
Additional resources:
Next, you need to enable modern authentication in your Office 365 tenant because it's required for conditional access. Modern authentication is enabled by default on Office 2016 clients and is currently rolling out for Exchange Online and SharePoint Online. To enable modern authentication for Office 2013, install the March 2015 Office Update Release.
Additional resources:
To enable modern authentication for Exchange Online in your tenant:
Set-OrganizationConfig -OAuth2ClientProfileEnabled $true
3. Verify that the change was successful by running the following:
Get-OrganizationConfig | ft name, OAuth*
To enable modern authentication for Skype for Business Online in your tenant:
Set-CsOAuthConfiguration -ClientAdalAuthOverride Allowed
3. Verify that the change was successful by running the following:
Get-CsOAuthConfiguration
Use the following cmdlet in Office 365 to prevent Office clients that use nonmodern authentication protocols from accessing SharePoint Online resources:
Set-SPOTenant -LegacyAuthProtocolsEnabled $false
Now that you’ve configured your tenant, users with client apps that support modern authentication have conditional access policies applied to them. Remember that currently, legacy applications and clients like ActiveSync will not be affected by conditional access policies.
You can block ActiveSync access to Exchange Online by configuring Mobile Device Access in the Exchange Admin Center. From the Mobile section, select Mobile Device Access and edit Exchange ActiveSync Access Settings. Set the Connection Settings to Block access and save.
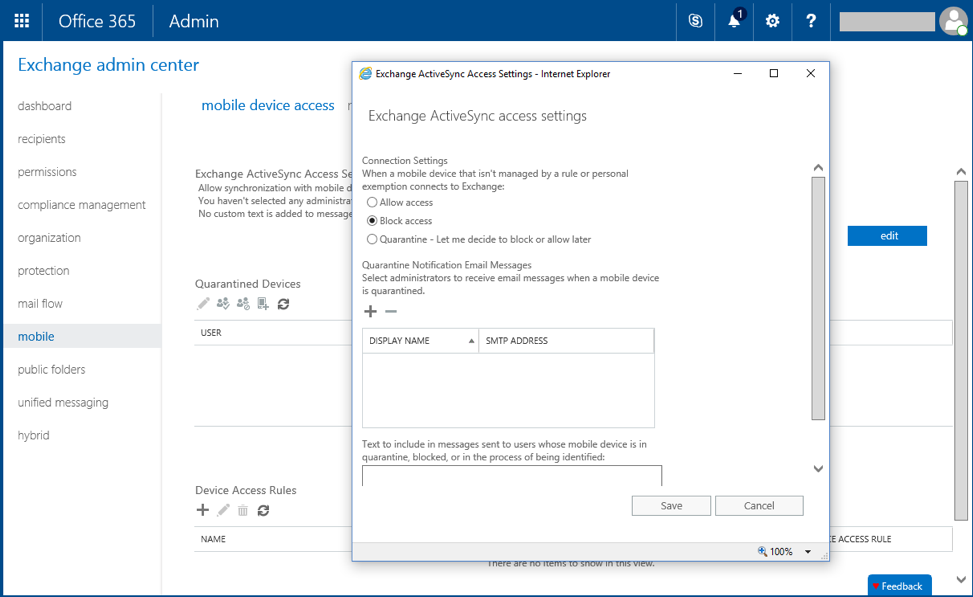
Preventing other legacy clients like Outlook 2010 or IMAP clients from accessing Exchange Online resources is more difficult. You either need to use a claims rule using a claims-based authentication solution like AD FS, or use Intune, which has its own set of requirements.
Additional Resources:
Here are a few takeaway points to summarize the hefty topic we covered above.
The following table shows the requirements, pros and cons for conditional access and claims-based rules.
The cloud is always changing. Developments are constantly being made to improve and overcome previous obstacles, but there are only so many things that can be done for legacy applications.
My bet is that Microsoft will continue to reduce the number of "supported" clients until only the latest and greatest clients and applications are supported — ones easily updated with fixes and new features that provide the best experience with Office 365.



For hybrid customers, Azure Active Directory Connect is one of the most important tools you need to...
